Contents:
Once payment is received, your account will be upgraded to Trader. It is the works of a few masterminds who have been in crypto, technology, coding space for a number of years and member of the teams have been a part of gala games in the past . However I can not say at what level the devs took part in that success but I can say they have treated this project as a top tier prospect going forward. Black gold Blackgoldrewards.com is an oil project looking to be the biggest oil backed crypto project to hit the blockchain space. The token page shows information such as price, total supply, holders, transfers and social links.
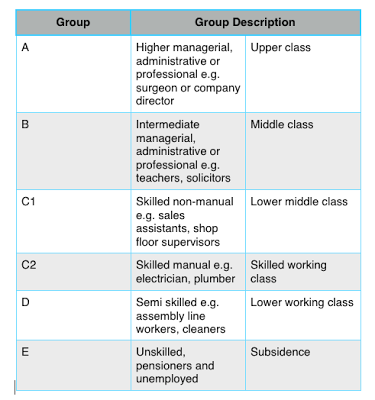
None of the respondents were classified into the Closeness to experience group, therefore a comparison of these groups can not be conducted. A universal approach for dividing colours has not been found yet. On the other hand, Ferwerda et al. attached orange, violet and yellow to the aforementioned set .
- In the design phase, a reference model-based user requirements elicitation process is designed .
- WORM-Drives are a hardware solution to this problem that prevents the deletion or alteration of written data, similarly to the blockchain, but without the decentralization aspect and without offering trustless transactions.
- In fact, it is outside of the scope of our main objective and additional research work would be necessary to this end.
- Nowadays, these cryptographic technologies found their way into everyday life and are used self-evidently without apparent knowledge of their existence by the common user.
- We described business requirements, as they occur in garages and body shops, with the concepts of business capabilities, business services and business processes.
- One speculation of this abandonment is that it requires a large number of tests to train the model.
Applied to an industrial digital transformation case study most of the proposed indicators could be operationalized and values could be captured. Also the indicators have been proved suitable for the determinants with exception of “business model”. In this context, the authors claim that some influencing factors and indicators were incorrectly represented or even missing within past researches. First, a further qualitative research approach might investigate more detailed factors or indicators. Second, the empirical research model should be proved by a quantitative approach. In addition, there are general limitations regarding our qualitative research design as there might be even more databases and valuable work (e.g. paper in supposedly poorer journals) to consider when reviewing literature.
Transferring the token to the creditor hinders the owner of the item from further transfers of property and thus secures the credit. At the same time, the creditor can easily block the smartphone by transferring the property token to an address unknown to the phone so that its functioning is effectively blocked, which gives the borrower a strong incentive to pay his rates. The creditor has no incentive to abuse the token except for its opportunistic retention after the credit has been paid back. However, backing the credit contract by a smart contract may exclude this risk too. If the credit has to be paid back on the same blockchain as property in the item is tokenized on , a smart contract may automatically trigger the return of the token to the borrower as soon as the loan has been paid back in full. Additionally, the smart contract may exclude any transfer of property by the lender for the time during which the borrower fulfils his duties from the credit contract.
Their successful finalization is a prerequisite for the functioning of the solution as presented. Furthermore, the initial solutions will most likely fall short of the centralized systems. Still, the suggested advantages exist on a theoretical level and the utilized decentral systems are under heavy development, fueled by public interest in and experimentation with cryptocurrencies and tokens. The limitations described above can best be characterized by Foster’s S-Curve for assessing technological threats, in which the current state of new technology is less capable than existing technology, but the new technology incorporates higher potential.
They are based on the cross- or industry-specific international experiences collected over many years and put together by practitioners in cooperation with scientists. These are not theories and on purpose are not directly derived from theories. Nevertheless, it is likely that one can find theories for justification of best practices . Therefore, the author suggests to investigate possible theoretical baselines for ITIL, e.g. its relation to organizational, behavioral, agency, and risk theories. This formalization approach would guarantee the benefits for both theory and practice (increasing applicability of research findings in the enterprise context). As rightly mention, there is in general a lack of theoretically driven research in the area of IT Service Management , where ITIL belongs to.
Food and Travel NFT Projects
Potential of the blockchain is otherwise only influencing the problem, not the solution as the necessity for audit processes already is the status quo. Francisco and Swanson emphasize the increasing competitive pressure by evermore informed consumers. They no longer solely demand attractive prices but additionally adequate product transparency. It is to be expected that not the existence of the blockchain itself will transform SCM, however that it much rather poses an answer to a consumer market evolving to seek an undeceived choice.
Once again the ZSK does not exist and the validation process passes with a single key (Line 28–30). This protocol provides us with origin authentication and message integrity. We reduce key management to a single certificate rather than multiple keys, making it simpler. However, the question on if RRSIGs suffer from IP fragmentation still exists. RRSIG records contain a digital signature DNSKEY records contain a signing key DS records contain the hash of a DNSKEY NSEC and NSEC3 records map a denial of existence to a domain range.
I hope it recovers but with the Beanie mess, just doesn’t seem very likely. CMyKatz – I really like the dev on this and the community rallied around him but it bgld coingecko just didn’t happen, a combination of bad timing on market sentiment and high gas fees. I have cMyKatz, cMyGravez, and ZombieKatz – they are all worthless now.
The next two steps are group discussions involving IT as well as business management. The expert who applied and evaluated the application of the framework in the third iteration confirmed the conclusiveness, applicability, and importance of the artefact. When analyzing the results to the question which of the following skills do you consider are important in your IT department?
Projects
It reveals that lots of recent effort is spent for online energy marketplaces and P2P energy transactions, which are both supportive for renewable energy communities as motivated in Sect. However, considering significant drop in hash rate with 20% lower voltages, the decrease by 15% proved to be better choice. Our findings suggest that for best hash rate of RX 480 video cards it is recommended to increase memory clock frequency (e.g., 2250 MHz). For tested RX 580 cards the default memory clock frequency proved to be the best setting. For minimizing power consumption, it is recommended to lower core voltage (e.g., 15%).
This paper describes the possible architecture for the interaction of sociocyberphysical systems components based on the integration of the cloud-based IoT platform and blockchain technology. Consumables consumption is proposed to be tracked through blockchain with smart contracts. For this purpose, the paper provides basic classification of consumables, and a possible way of their representation with blockchain tokens, taking into account the specific characteristics of each of their classes.
Paper already identified some methods on the use case evaluation in the context of AI implementation for process automation. Those are widely used by vendors and business consulting companies. The focus of the current research, ITIL framework, as well as many other frameworks, e.g. CMMI , COBIT , eTOM , can be fairly classified into best practices.
Link your account with our Telegram bot to receive customizable crypto alerts. Unlike most crypto bots, you create and manage alerts from our web interface. Please keep this window open and allow some time for the transaction to be confirmed. We do not accept payments over the BNB or BSC network, please use ETH when sending ETH, USDC or DAI.
Other types of reference models (e.g., goalbased reference model) and other types of user requirements elicitation techniques might be useful as well, and should be investigated in future studies. This research, therefore, makes several contributions to the current BDA research base. First, our study contributes to the emerging literature of capturing the business value of BDA investments . Second, we examined the different configurational forms in which firms generate business value from BDA. Finally, this study synthesized the CBDACM from the literature and subsequently extended and validated this model through interviews with big data field experts and consultants. Moreover, our configurational model highlights the importance of different configurations of resources tailored per phase.
Alerting MethodsNotification Settings
Moreover, in order to receive inputs for the development of the framework, a literature research regarding frameworks and models in the context of Digital Transformation has been performed. The findings of the first phase were analyzed to suggest a first draft of the framework for evaluation. However, based on several expert interviews and workshops with companies, an evaluation of the framework took place to finalize the artefact with the inputs from the evaluation phase. The research is embedded within the topic of Digital Transformation and not on the digitization of a business, thus, the technical assessment tools are not being compared as part of this research.
First there is a check whether there are cloud services which correspond with the capabilities and business services of a specific use case. If the answer is yes, then we check in a second step if there are cloud services which satisfy the requirements on business process level. However, there is a lack of focus in BITA on the external environment of the companies.
Support & Legal
Given sheer rise of popularity of cryptocurrency mining, the demand for capable hardware skyrocketed and induced fierce competition among hardware manufacturers. The shift from CPU to GPU based mining was followed by more specialized hardware pieces such as FPGA and ASIC. The history of this hardware evolution is explored in excellent review of Taylor . Although presently Bitcoin is mostly mined by using ASIC, Ethereum is still mined with GPUs. The problem there is a shortage of scientifically tested experiments looking for best settings of different GPU parameters.
This might also lead to further data feature types prediction efficiency analysis. These actions may improve further models performance and precision. After having an ability to precisely predict churners, further retention actions must be taken. Different retention strategies may be applied for specific groups of potential churners (as described in Sect. 4) to improve their success rates. These strategies should also be part of the research with a primary goal of finding the best-performing ones.
The problem of interaction of two separate blockchains is examined closely in , where the author introduces several ways to enable cross-chain operability. A relay has been described and implemented in the BTC Relay system5 , which allows users to pay for execution of smart contracts on the Ethereum network with Bitcoins. While the exchange of the funds on different blockchains is not the primary aim of this system, it could be extended to support this use case. 6 Discussion and Conclusion The usefulness of the dynamic capability approach for BITA improvement has been highlighted in literature . This literature also notes that co-development of business and IT can support BITA improvement. However, little is known about how a specific dynamic capability, i.e., BPM, with the aim of BITA improvement can be enhanced and how it can enable the co-development.
Ontologies to be used in modeling have been created, such as or . This knowledge representation and reasoning framework becomes especially useful in situations in which knowledge from multiple fields must be taken into account at the same time, as is the case for blockchain environments. The researchers implemented a protocol which turns the blockchain structure into a trust-less automated access-control manager, which is done https://cryptolisting.org/ by combining the blockchain and off-chain storage. To accomplish this the user has to install an application which uses this privacy platform, as the user signs up for the first time an identity is generated and sent along with the permission settings to the blockchain. The data collected on the device is encrypted with the identity and sent to the blockchain along with appropriate encryption details from the off-chain storage.
However, the process innovation possibilities that blockchains entails for energy markets are currently focused on peerto-peer trading scenarios and the integration in energy markets. This paper provides a major contribution in form of blockchain-based process management of transactions between microgrid energy assets. The approach goes beyond previous ones, as tokenization enables a multitude of use case applications such as grid management, energy product certification or the integration of electric vehicles. Using blockchain platform design ontologies , we will outline the components of our smart contract ecosystem for the digital energy asset management in the subsequent section. And logistics processes are integrated intelligently across company boundaries to make manufacturing more efficient and flexible.
No responses yet